If someone forwarded you this briefing, sign up here to get the Index Insider every Friday.
CYBERSECURITY IN MANUFACTURING
Cybersecurity is a hot-button issue for any company undergoing IT transformation. Nowhere is this truer than in the major transformations occurring in the world’s largest manufacturers. It’s in the process of adopting smart manufacturing practices – which is to say leveraging technology to measure, monitor and improve product design, manufacturing processes and supply chains – that these companies are running into real cybersecurity challenges. Transitioning from legacy manufacturing to smart manufacturing involves a great deal of IT infrastructure and software to connect systems to the network or internet that have not previously been connected. This includes everything from the programmable logic controllers (PLCs) running assembly lines to the controls on individual machines.
The promise of this transition for manufacturers includes cost savings, efficiency and better performance in the manufacturing process, but the risks are real. Very few of the legacy operating technology (OT) systems were built with a security-first mindset. Instead, they use physical device access as the first line of defense. Once these systems are connected to a company’s IT network, the cybersecurity surface grows – and the job of managing that surface expands outside of IT.
In our recent survey of smart manufacturing adoption, we found that IT is often not the sponsor of smart manufacturing initiatives. The four most-common sponsors for smart manufacturing are executives overseeing supply chain, production and product engineering and then the CTO. The CIO ranks fifth. This means smart manufacturing initiatives are being led by the business, not IT.
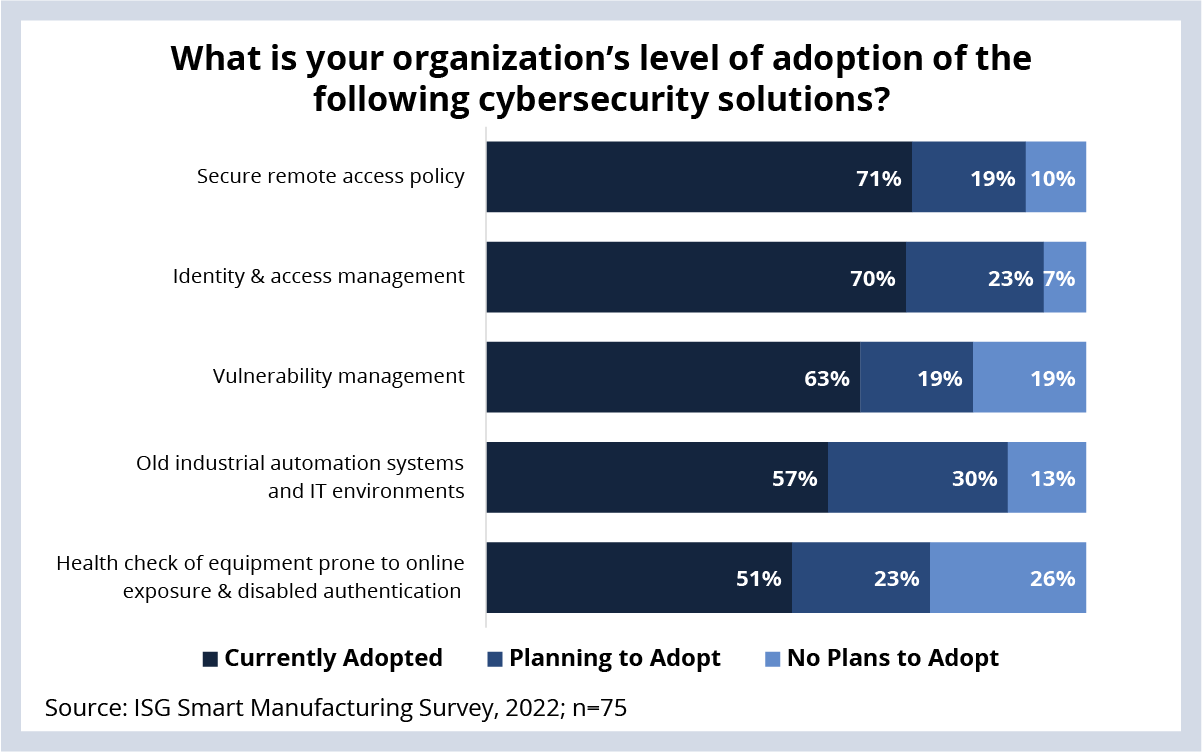
When we asked about adoption of cybersecurity solutions, we found that IT systems are being more aggressively protected – or at least invested in – with cybersecurity solutions than the manufacturing systems themselves (see Data Watch).
Like so many digital transformations over the last few years, the business is leading the way. But it is critical that IT remain heavily involved to manage the cybersecurity implications of new business models and technologies.
DATA WATCH
CONTRACTING ACTIVITY
M&A ACTIVITY
- Broadcom announces plans to buy VMWare (link).
