In today's hyperconnected world, every enterprise faces cyberattacks. It’s crucial to have a robust incident response plan when an incident occurs. Digital forensics and incident response, or DFIR, integrates two key disciplines to streamline investigations and mitigate cyber threats effectively. Digital forensics is the investigation of cyberthreats that can be used for various sources, such as legal proceedings, internal investigations and understanding the scope of the attack; incident response focuses on detecting, containing, and mitigating cyberattacks as they are happening to minimize damage and restore normal operations as quickly as possible. When these two are brought together, DFIR goes beyond simply patching the breach; it allows a company to uncover the root cause, mitigate damage, preserve evidence and prevent future attacks.
5 Reasons Businesses Need DFIR
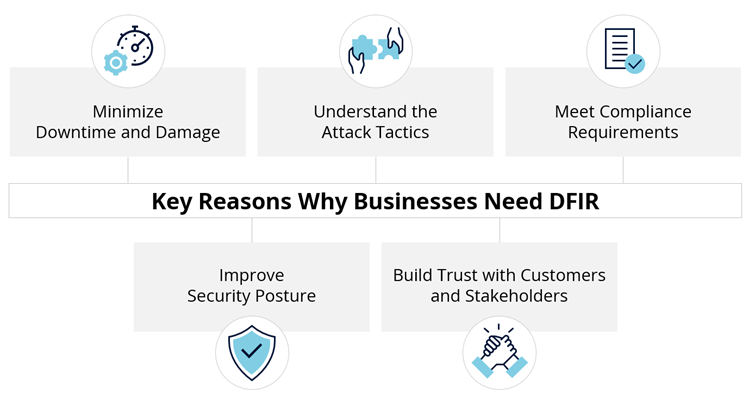
Robust DFIR capabilities are strategic assets. They provide the following four important benefits:
- Swift response and mitigation: Efficient DFIR capabilities ensure quick isolation of affected systems, minimizing financial losses and operational disruptions. This agility is crucial to maintaining business continuity and reducing potential damages.
- Insights for preventive measures: By deciphering attack methods and motives, DFIR capabilities empower businesses to fortify their defenses against similar future threats and bolster overall security measures.
- Regulatory compliance: Strong DFIR strategies help fulfill compliance requirements and ensure organizations meet regulatory demands. This not only mitigates legal risks but also helps avoid potential financial penalties.
- Improved trust and reputation: A transparent and effective DFIR response signals a commitment to data security, enhancing trust with customers, partners and stakeholders. Trust building is fundamental for maintaining business relationships and preserving a positive reputation.
The Evolution of Digital Forensics Is Moving Toward Incident Response
While both digital forensics and incident response deal with security breaches, they have distinct functions and approaches. The investigative nature of digital forensics plays a crucial role in differentiating it from incident response. Digital forensics delves deeper, analyzing more data sources and employing forensic techniques for detailed reconstruction, while incident response prioritizes efficiency and focuses on key evidence for immediate action.
Together, DFIR plays a critical role post-incident by providing a systematic approach to handling and mitigating the fallout of a cybersecurity breach. Once an incident occurs, DFIR specialists investigate, contain, analyze and ultimately respond to the incident. They meticulously collect and analyze digital evidence to understand the scope, nature and extent of the breach. This involves forensic examinations of affected systems, identifying the attack vectors and determining the root cause.
DFIR experts help contain and eradicate the threat, working to minimize the impact on affected systems and networks. DFIR professionals also contribute to regulatory compliance by documenting the incident and ensuring a thorough understanding of its implications, which can be crucial for legal and regulatory requirements. Their expertise and methodologies are instrumental in responding effectively to incidents and restoring the security posture of affected organizations.
DFIR for Proactive Threat Defense
While traditionally carried out post-incident, DFIR capabilities should be harnessed for proactive defense, by using it to understand the root cause of events and prevent their recurrence coupled with comprehensive threat hunting. This involves analyzing past incidents, proactively hunting for hidden threats, leveraging threat feeds, crafting tailored threat models, refining security controls, educating employees and optimizing incident response plans. A shift toward a proactive stance is crucial in today's ever-evolving cyber threat landscape.
As per the NIST framework, the incident response lifecycle is outlined in four key phases: preparation; detection and analysis; containment, eradication and recovery; and post-incident activity.
Four Key Phases of the Incident Response Lifecycle
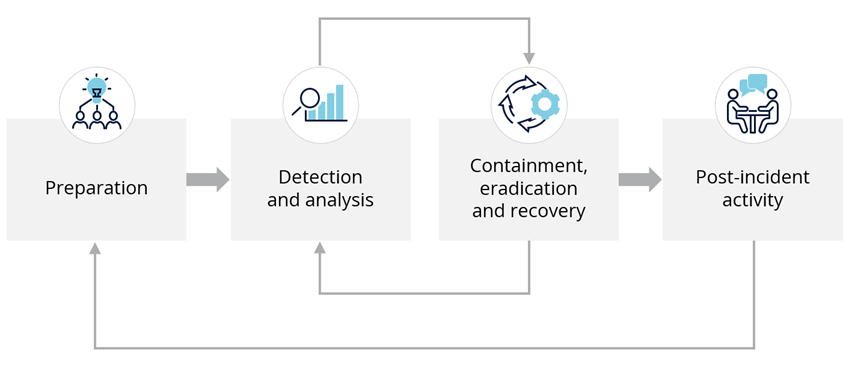
The incident response cycle operates as an ongoing process rather than a linear project. Following the final step of post-incident activity, the critical focus is on assimilating the learned lessons into the subsequent preparation phase. Insights from analyzing the incident aftermath enhance the organization's readiness against future threats. They contribute significantly to refining strategies, reinforcing the defense and strengthening response protocols during preparation. This continual flow of insights feeds into the cycle, ensuring a consistent evolution toward a more robust and resilient security approach.
DFIR as the Bridge: Connecting Investigation, Detection and Response for Enhanced Security
Integrating DFIR with other existing security tools – including security orchestration, automation and response (SOAR); security information and event management (SIEM); and extended detection and response (XDR) – creates a synergistic cybersecurity ecosystem. This fusion empowers enterprises to move beyond reactive defense and toward proactive threat detection, mitigation and continuous learning.
DFIR is the investigative arm, meticulously analyzing forensic evidence to understand attack vectors and root causes. XDR provides broad attack visibility across endpoints, networks and the cloud. SIEM aggregates logs and contextualizes historical data, aiding in threat hunting and incident reconstruction. The agile executor, SOAR, automates routine tasks and implements DFIR-defined response playbooks, minimizing disruption and accelerating recovery.
This collaborative approach yields tangible benefits:
- Enhanced threat detection: XDR's comprehensive view, enriched by DFIR insights, leads to faster and more accurate threat identification.
- Deeper incident understanding: DFIR's forensic expertise unravels the attack narrative, informing effective containment and eradication strategies.
- Proactive vulnerability mitigation: DFIR findings refine XDR and SIEM detection rules, preventing future attacks with similar tactics.
- Continuous security evolution: Post-incident analysis optimizes the SOAR playbook and knowledge sharing across all tools, strengthening the overall security posture.
By embracing this integrated approach, enterprises can transition from passive vulnerability management to a proactive, threat-aware security posture, safeguarding their critical assets and confidently navigating the ever-changing cyber landscape.
How to Choose the Right DFIR Provider
Selecting the right DFIR provider is a critical decision that significantly impacts the outcome of incident response efforts. Central to this selection is a provider’s availability, necessitating a 24/7 operational presence to swiftly and effectively mitigate incidents, minimize potential downtime and damage. Equally crucial is the expertise of the team. You’ll need certified professionals adept at forensics and incident response and well-versed in the latest technological advances.
A proficient provider will use advanced tools, have ready access to comprehensive threat intelligence and conduct thorough investigations that unravel the depth and scope of an incident. Their approach to communication and reporting is equally vital, with regular updates and detailed reports facilitating a clear understanding of the incident's nature and severity, guiding informed decision-making throughout the response process.
Moreover, an indispensable attribute is the provider's commitment to data privacy and security. Adhering to stringent standards to safeguard sensitive information and protect organizational data is imperative. These collective attributes form the pillars of a reliable and effective DFIR provider.
Why Skilled DFIR Professionals Are the Most Valuable Tool
In cybersecurity, while tools and techniques are crucial, the role of DFIR experts is pivotal. These professionals, with vital human traits such as intuition, experience and critical thinking — attributes essential in deciphering intricate cases and averting future breaches – become the cyber investigators.
DFIR professionals transcend the role of operators; they function as seasoned investigators acquainted with attackers' methodologies. Their proficiency enables them to anticipate and adapt strategies, delving beyond algorithms to assemble fragmented evidence and unveil core issues and their repercussions. DFIR professionals proactively identify hidden threats, predict emerging attack vectors and precisely customize responses for each incident.
Their influence extends beyond technical prowess; during cyber crises, DFIR experts communicate across various domains, elucidating complex technicalities in a language accessible to diverse stakeholders. DFIR professionals orchestrate cohesive collaborations that minimize the impact of incidents and preserve an organization's standing.
Of course, the battle against cyberthreats is continuous. DFIR professionals adopt a perpetual-learning approach, refining their skills, seeking innovative methodologies and sharing insights to fortify the collective resilience of the cybersecurity community.
DFIR encompasses far more than reactive incident management. It serves as a proactive safeguard and resilient cyber defense. Integrating a DFIR solution within broader security frameworks and selecting a suitable provider empowers businesses to transcend from vulnerable targets to adept navigators of the dynamic cyber landscape. Enterprises should recognize that investing in DFIR signifies more than a mere expenditure; it symbolizes an investment in resilience, expansion and confidence in the digital era.
ISG helps enterprises navigate the rapidly changing cybersecurity provider market and find a right provider. Contact us to get started.
