A Cybersecurity Strategy Must Constantly Evolve
As companies expand the ways they communicate, network, store data, automate and digitize, they must continually mature and evolve their cybersecurity strategies. Ever-increasingly sophisticated cyber threats are forcing companies of all sizes and industries to take a closer look at how they are organizationally aligned and how to enhance their cybersecurity risk posture.
Of course, evolving your cybersecurity strategy comes with financial implications. While new technologies help to automate and capture many of the threats up front, organizations must figure out how to hire, train and retain skilled employees to architect, manage and support these technologies.
Cybersecurity Sourcing Trends
While CIOs are trying to reduce and optimize costs in their organizations, CISOs are needing investments to secure the environment through new tools and sourcing initiatives. And, as the threat landscape widens, cybersecurity costs go up. In fact, cybersecurity should be 5% - 13% of overall IT spend. The more regulated the organization, the higher the percentage needs to be. For nearly every enterprise, this percentage has increased year over year and will likely continue to increase.
The current trends in cybersecurity sourcing include the following:
- Security is increasingly a standalone sourcing transaction.
- Organizations are involving security earlier in DevOps, infrastructure designs, cloud migration and adoption, to look for shift-left strategies that reduce costs but do not increase risk.
- Cybersecurity scope in organizations is increasing to include security services that are currently supported in other infrastructure stacks, new technologies to proactively identify threats and automation to eliminate threats and reduce redundant efforts.
- Leaders are modifying service-level agreements to support expanded scope and measure the effectiveness of managing threats.
- Organizations are focusing more on governing functions for stronger governance, cybersecurity risk management, compliancy and resiliency.

Figure 1: Current Cybersecurity Sourcing Trends
Expanding Scope for Cybersecurity Sourcing Deals
The role of the CISO has been expanding, and the scope of cybersecurity has also. What was once spread out in the IT organization is now more centralized. While security is everyone’s responsibility in the organization, centralizing a security function helps address challenges in a holistic way and ensure your organization is secure.
As companies see the benefits and necessity of this approach, they seek to consolidate functions. Over the past two to three years, we have seen cybersecurity teams expand their scope from basic L1 SOC/SIEM to much more advanced functions, such as identity and access management integration services and automation and orchestration advancements in security operations.
ISG uses functional decomposition charts (see Figure 2) to rapidly help a client
outline as-is capabilities and identify a strategy and sourcing decisions.
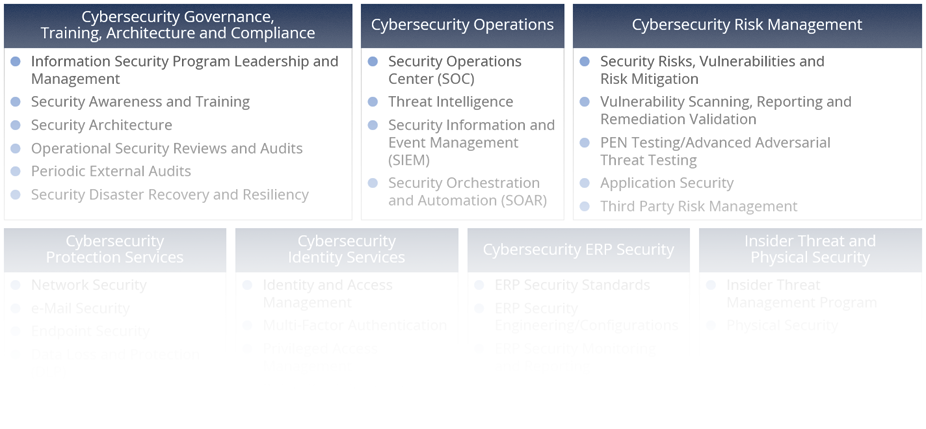
Figure 2: Scope of Cybersecurity Sourcing Transactions
Put all this together – the pace of technology change, mounting financial pressure, the need to retain skilled resources and the widening of the scope of cybersecurity – and CISOs are looking to source cybersecurity functions.
ISG works with enterprises to help design a cybersecurity strategy and then assess what to source and what to retain. We have the expertise to help secure your environment. Contact us to find out how we can help.
